SIEM (Security Information and Event Management) is your organization's security radar system. While regular monitoring tools tell you when systems break, SIEM tells you when you're under attack.
It collects security data from your network—from firewall logs to user logins—and analyzes it to detect threats in real time.
Let's explore how SIEM works, why you need it, and how to implement it effectively.
What is SIEM? #
SIEM systems serve as the central nervous system of an organization's security infrastructure.
While observability tools identify "what's broken" in your systems through metrics, traces, and general logs, SIEM focuses on detecting "what's malicious" by analyzing security-relevant logs and events.
At its core, a SIEM system collects, processes, and analyzes security-specific data across an organization's network. It primarily ingests security logs and events from various sources, including:
- Firewalls and network security devices
- Cloud infrastructure security logs
- Identity provider authentication logs
- Endpoint security solutions
- Application security logs
- System security events
The primary goal is to detect and respond to potential security threats in real-time while providing historical analysis capabilities for incident investigation.
Benefits of SIEM #
Security Information and Event Management (SIEM) systems provide several critical advantages for organizations looking to strengthen their security posture. Based on real-world implementations and insights from industry practitioners, here are the key benefits organizations can expect:
Real-Time threat detection #
SIEM systems enable organizations to detect and respond to potential threats as they happen. This capability is essential for providing 24/7 monitoring and proactive threat protection, especially for organizations that lack large internal security teams. Modern SIEM systems can process massive volumes of security data - potentially billions of events daily - to maintain effective security monitoring.
Centralized security monitoring #
SIEM acts as a centralized hub for security data, consolidating information from multiple sources into a single, manageable platform. Organizations can collect and analyze data from numerous sources across their infrastructure.
This includes security-relevant information from firewalls, cloud infrastructure, and identity providers, as well as logs from security devices, applications, and system events. This centralization makes maintaining a comprehensive view of an organization's security posture possible.
Historical analysis capabilities #
SIEM systems provide robust historical analysis capabilities for incident investigation. Security teams can investigate incidents after they occur, review user activities when issues are reported, and perform historical queries for security analysis and pattern detection. This historical perspective is crucial for understanding security incidents and improving future security measures.
Cross-System correlation #
One of the most powerful benefits of SIEM systems is their ability to correlate events across different systems. Security teams can query across diverse data sets and track activities across multiple systems.
For example, when investigating suspicious activity, analysts can track an IP address's activities across different systems, providing a comprehensive view of potential security threats. This correlation capability helps identify patterns and connections that might otherwise go unnoticed.
Compliance support #
SIEM systems help organizations meet their compliance requirements, particularly around data retention. Many organizations need to retain security data for extended periods, sometimes up to seven years and SIEM systems provide the necessary infrastructure to manage this long-term storage effectively. This capability ensures organizations can demonstrate compliance with regulatory requirements while maintaining searchable access to historical security data.
The effectiveness of these benefits depends on proper implementation and management of the SIEM system, including careful consideration of data sources, retention policies, and analysis requirements. Organizations must balance these capabilities against their specific security needs and resource constraints.
Challenges of SIEM #
While SIEM systems are crucial for modern security operations, they come with significant challenges that organizations must address. Here are some of the most critical challenges organizations face when implementing and maintaining SIEM systems:
Data volume #
SIEM systems must process an ever-increasing deluge of data from numerous sources, including firewalls, cloud infrastructure, identity providers, and countless other devices. This constant influx of logs and security data creates significant performance challenges.
The sheer quantity of information that must be processed, stored, and analyzed can quickly become overwhelming, leading to performance bottlenecks and escalating costs. Organizations must carefully balance how much data to retain in active storage versus archival storage while maintaining effective threat detection capabilities.
Data variety and normalization #
Security data comes in numerous formats—Syslog, JSON, plain text, and various proprietary formats—each with its unique structure. This lack of uniformity requires organizations to develop custom parsers and schemas to standardize the data. Identifying threat patterns and anomalies becomes difficult without proper normalization, and the SIEM becomes less effective at detecting threats. The complexity of managing multiple data formats and ensuring consistent data structure adds significant overhead to security operations.
Cost management #
The financial implications of operating a SIEM can be substantial, particularly when dealing with large datasets. As data volumes grow, so do the costs associated with processing, storing, and analyzing that data. This challenge is particularly acute for small and medium-sized businesses (SMBs) that need enterprise-level security capabilities without enterprise-level budgets. The costs include storage and processing, specialized hardware, software licenses, and skilled personnel needed to maintain the system.
Scaling challenges #
Traditional SIEM solutions often struggle to scale efficiently as data volumes grow. The architecture of many systems is not designed to handle exponential increases in data, leading to performance degradation and increased operational costs. Scaling typically requires adding more hardware or software components, which introduces further complexity and requires additional maintenance. Organizations must carefully consider how their SIEM solution will grow with their needs while maintaining performance and cost efficiency.
System complexity and maintenance #
The complexity of implementing and managing a SIEM is a significant challenge in itself. It requires integrating numerous data sources, maintaining custom parsing rules, developing schemas, and providing ongoing maintenance. Regular updates, patching, and system optimization are necessary to ensure the SIEM operates correctly and keeps pace with evolving threats.
This complexity increases the risk of human error, requires skilled personnel, and can consume significant resources. These challenges are interconnected - addressing one often impacts the others. For example, improving data processing capabilities to handle larger volumes might increase system complexity and costs. Similarly, implementing better data normalization might require more processing power and impact scaling capabilities. Success with SIEM implementation requires carefully balancing these competing demands while ensuring the system meets current security and future scalability requirements.
Components of a SIEM system #
A Security Information and Event Management (SIEM) system is a complex solution that collects, processes, and analyzes security data from across an organization's infrastructure. By combining multiple components into an integrated system, SIEM enables organizations to detect and respond to security threats while maintaining visibility into their security posture. Here are the key components that make up a modern SIEM system:
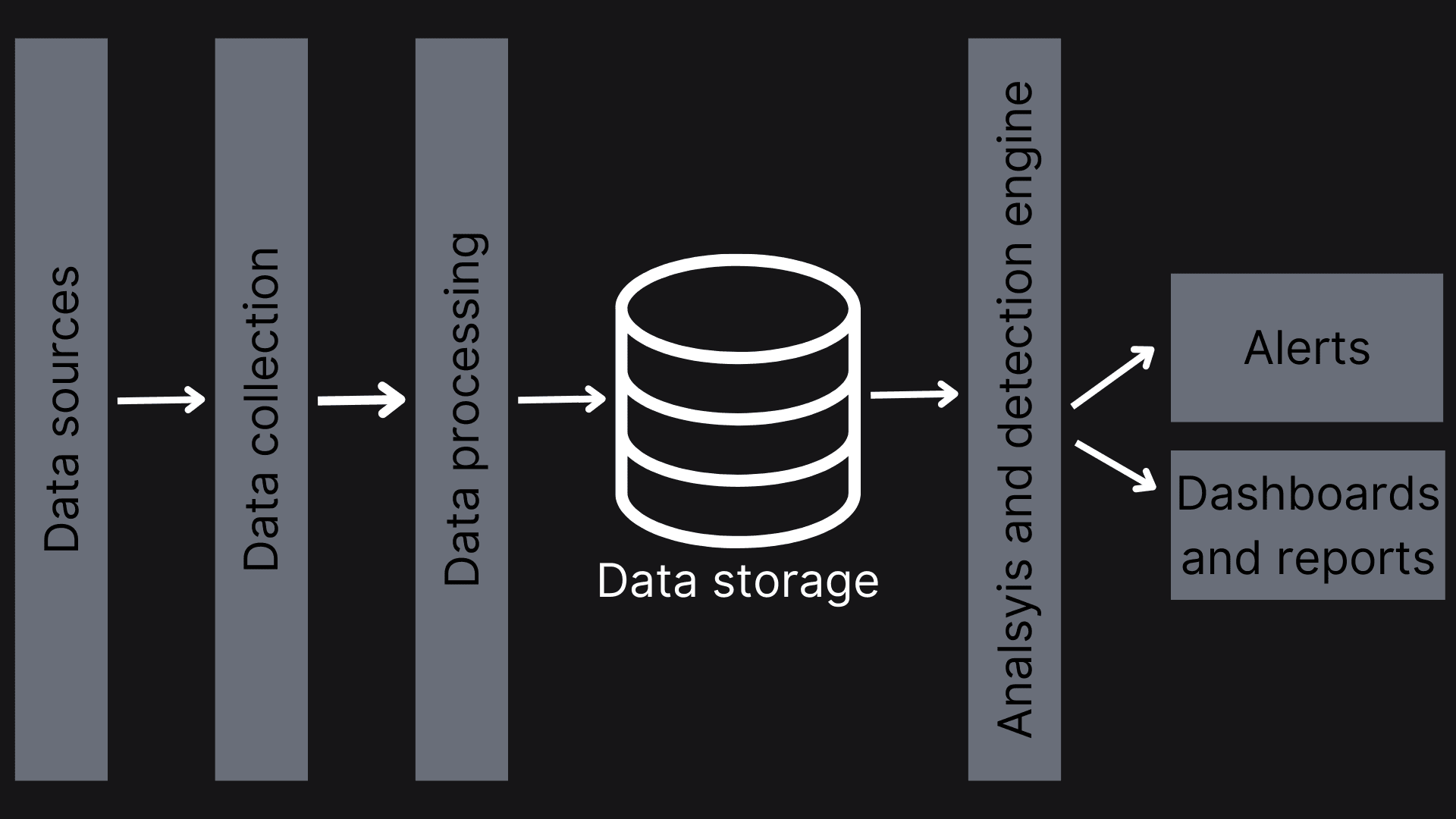
Data Sources #
The foundation of any SIEM system is its data sources. These include various systems and applications that generate security-relevant information, such as firewalls, cloud infrastructure, identity providers, application logs, system security events, and network devices.
Each source provides crucial information that, when combined, creates a comprehensive view of an organization's security landscape.
Data collection #
The data collection component serves as the ingestion point for all security data. It handles the crucial task of gathering information from various sources, managing different input formats, and ensuring reliable data ingestion. This component must be robust enough to handle high-volume data streams while maintaining data integrity and preventing loss.
Data processing #
Once collected, raw data must be processed into a standardized format. The data processing component handles the normalization, enrichment, and transformation of security data. It ensures that common fields are standardized across all sources, adds relevant security context, and prepares the data for efficient storage and analysis.
Data storage #
The storage component serves as the central repository for all security data. It must efficiently manage active and historical data while providing fast query capabilities. The storage system needs to balance compression for efficient storage with quick access for analysis, often retaining data for extended periods to meet compliance requirements.
Analysis and detection engine #
This component analyzes security data to identify threats and anomalies. It runs continuous detection rules against incoming data, correlates across different data sources, and supports automated and manual security investigations. The engine combines real-time analysis with historical data to identify security incidents and potential threats.
Alerts #
The alerting component converts detected security issues into actionable notifications. It manages the crucial task of informing security teams about potential threats and ensuring that critical security events are properly communicated and tracked. This component often includes alert prioritization, routing, and integration with incident response workflows.
Dashboards and reports #
The dashboards and reports component provides visibility into the security environment through visualizations and structured reports. It enables security teams to monitor their security posture, investigate incidents, and understand trends through interactive dashboards and detailed reports. This component is essential for both day-to-day security operations and longer-term security planning.
These components create an integrated system that enables organizations to effectively monitor, detect, and respond to security threats while maintaining comprehensive visibility into their security posture. The success of a SIEM implementation depends on how well these components work together and how effectively they're tuned to an organization's specific security needs.
Best practices for SIEM #
Drawing from our own experience as well as industry experience and successful implementations, here are key best practices that organizations should consider when deploying and maintaining their SIEM systems:
Data collection and processing #
Effective data collection starts with early normalization in the pipeline to ensure consistency across all sources. Security teams should enrich logs with relevant security context during processing, making them more valuable for analysis. Regular monitoring of data source health and collection pipelines and tracking data volumes and collection metrics is crucial. Organizations should implement proper data source configuration management to maintain the reliability and consistency of their data inputs.
Storage optimization #
Storage strategy should consider time-based partitioning for efficient data management, allowing organizations to handle recent and historical data effectively. Implementing appropriate data retention policies helps balance compliance requirements with storage costs. Organizations must consider the trade-off between compression and query performance while continuously monitoring storage capacity and growth. Planning should account for both hot and cold storage needs, ensuring cost-effective long-term data retention.
Detection strategy #
A successful detection strategy typically begins with implementing out-of-the-box detections and then customizing them to match specific organizational needs. Maintaining detections as code enables version control and consistent deployment. Detection rules should leverage correlation across multiple data sources to identify complex threats. Teams should focus on high-value security signals that matter most to their organization while regularly reviewing and tuning detection rules to minimize false positives.
Alert Management #
Alert configuration requires careful consideration of thresholds to avoid alert fatigue while ensuring critical issues are noticed. Organizations should implement alert routing to ensure notifications reach the appropriate teams. Daily summary reports often prove more effective than immediate alerts for non-urgent issues. Regular monitoring of alert effectiveness and tuning helps maintain the right balance. Integrating workflow tools like chat applications or ticketing systems streamlines the response process.
System monitoring #
Comprehensive system monitoring should cover both health and performance metrics. Teams must track query performance, ingestion rates, and system latency to ensure optimal operation. Setting up alerts for system issues helps prevent service disruptions, while regular health checks across all components ensure reliable operation. This monitoring should provide both real-time awareness and historical trending for capacity planning.
SIEM use cases #
SIEM systems serve multiple critical functions in modern security operations. Based on our analysis of real-world implementations, here are the five most important use cases:
Intrusion detection and prevention #
SIEM systems excel at monitoring network traffic and system activities to identify unauthorized access attempts. Modern platforms like RunReveal automatically detect anomalies and compromises across the environment while providing the necessary context for security teams to respond effectively. This capability forms the foundation of any robust security monitoring program.
Security monitoring and log analysis #
At its core, SIEM technology centralizes and analyzes log data from various sources. As demonstrated by both Huntress and Dassana's implementations, effective log management enables security teams to collect, normalize, and analyze data from multiple sources - from cloud services to network devices. This comprehensive view is essential for understanding the organization's security posture.
Threat detection and response #
Modern SIEM platforms excel at identifying and responding to various threats through pattern recognition and behavior analysis. This includes detecting malware, identifying suspicious user activity, and correlating security events across different systems. As seen in our own implementation with RunReveal, the ability to write custom detection rules and automate responses is crucial for maintaining effective security operations.
Compliance monitoring and reporting #
SIEM systems help organizations meet regulatory requirements by providing comprehensive logging and reporting capabilities. Dassana's implementation shows how SIEM can track security metrics, generate compliance reports, and monitor SLA violations across business units. This capability is essential for organizations that need to demonstrate compliance with standards like GDPR, HIPAA, or PCI-DSS.
Network anomaly detection #
SIEM platforms can identify unusual activities that may indicate security threats by analyzing network traffic patterns and system behaviors. As demonstrated by Huntress's work with millions of endpoints, modern SIEM systems can process massive amounts of network data to detect real-time anomalies, enabling quick responses to potential security incidents. These use cases demonstrate how SIEM systems have evolved from simple log management tools to comprehensive security platforms that provide critical capabilities for modern security operations. While other use cases exist, these five represent the core functions that make SIEM an essential component of enterprise security infrastructure.
Conclusion: building an effective SIEM strategy #
Implementing a SIEM system is crucial in modernizing security operations, but success requires careful planning and ongoing optimization. As we've seen through real-world examples from organizations like Huntress and Dassana, an effective SIEM implementation balances several key factors:
- A clear understanding of fundamental SIEM concepts and benefits
- Recognition and planning for common challenges
- Well-architected components working together seamlessly
- Focus on high-value use cases that align with security goals
- Implementation of proven best practices
The key to success lies in selecting the right technology and building a comprehensive strategy that addresses your organization's specific security needs while maintaining operational efficiency.
Whether implementing a new SIEM or optimizing an existing deployment, focusing on these core aspects will help ensure your security operations remain effective and sustainable. By understanding these fundamental aspects of SIEM systems, organizations can better protect their assets, detect threats more effectively, and maintain compliance with regulatory requirements while managing costs and complexity.