プライベートネットワークのセットアップ
ClickHouse BYOC は、セキュリティを強化し、自社サービスとの直接接続を可能にするため、さまざまなプライベートネットワーキングオプションをサポートしています。このガイドでは、自社の AWS または GCP アカウント内の ClickHouse Cloud デプロイメントを、社内アプリケーションや分析ツールなどの他のネットワークやサービスに安全に接続するための推奨アプローチを順を追って説明します。ここでは、VPC Peering、AWS PrivateLink、GCP Private Service Connect などのオプションを取り上げ、それぞれの主な手順と考慮事項を概説します。
ClickHouse BYOC デプロイメントへのプライベートネットワーク接続が必要な場合は、このガイドの手順に従うか、より高度なシナリオについては ClickHouse Support にお問い合わせください。
VPC ピアリングをセットアップする (AWS)
ClickHouse BYOC 用の VPC ピアリングを作成または削除するには、次の手順に従います。
ClickHouse BYOC 用のプライベートロードバランサーを有効化する
ClickHouse サポートに連絡して、Private Load Balancer を有効化してください。
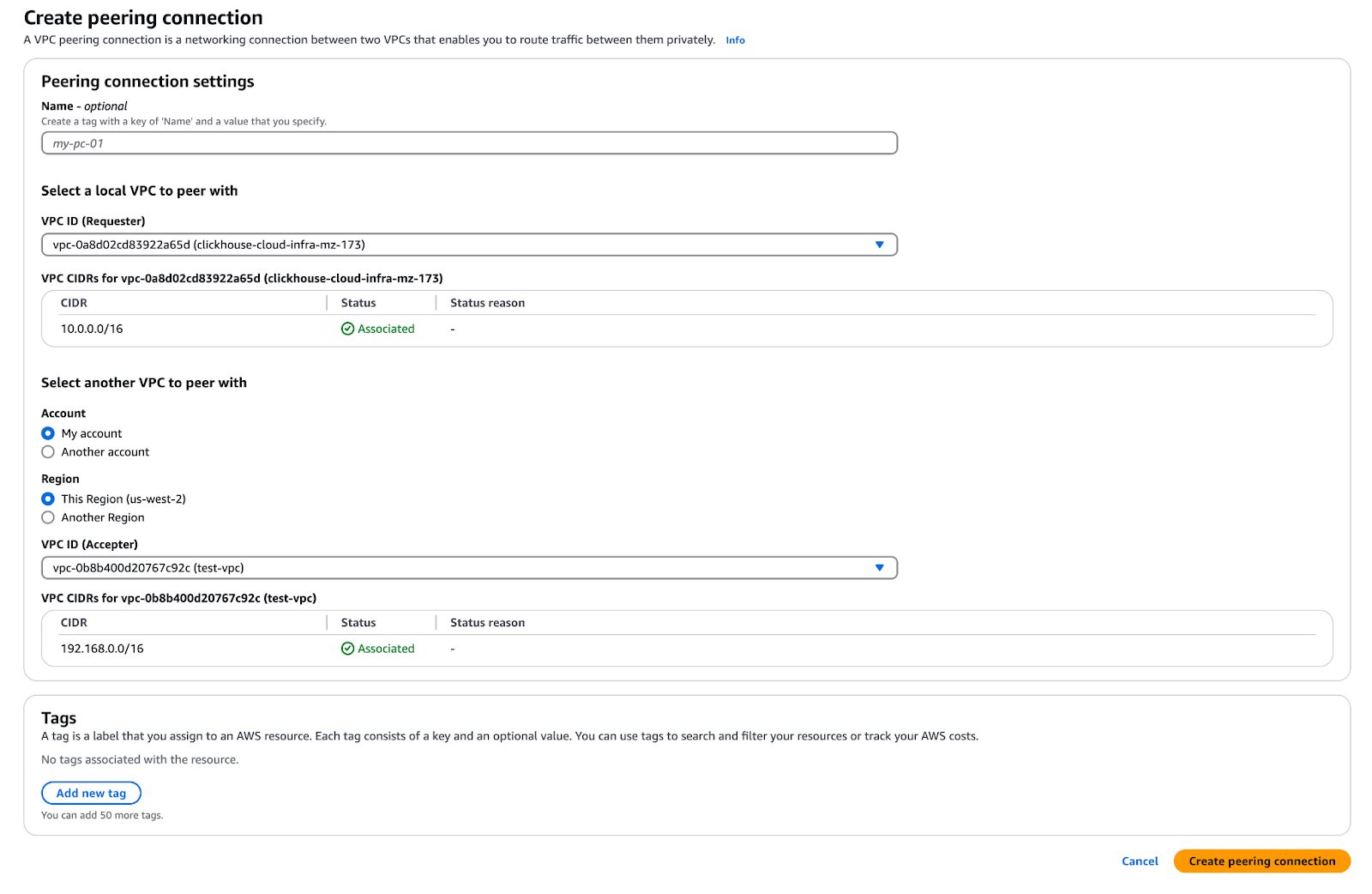
ピアリング接続を作成する
- ClickHouse BYOC アカウントで VPC ダッシュボードに移動します。
- 「Peering Connections」を選択します。
- 「Create Peering Connection」をクリックします。
- VPC Requester に ClickHouse の VPC ID を設定します。
- VPC Accepter に対象 VPC ID を設定します(必要に応じて別アカウントを選択)。
- 「Create Peering Connection」をクリックします。
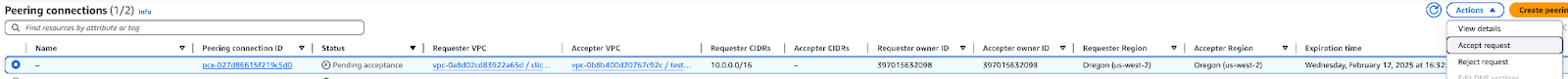
ピアリング接続要求を承認する
ピアリング先のアカウントで、(VPC -> Peering connections -> Actions -> Accept request) ページに移動し、この VPC ピアリング要求を承認します。
ClickHouse VPC のルートテーブルに宛先を追加する
ClickHouse BYOC アカウントで、
- VPC ダッシュボードの「Route Tables」を選択します。
- ClickHouse の VPC ID を検索し、プライベートサブネットに関連付けられている各ルートテーブルを編集します。
- 「Routes」タブの「Edit」ボタンをクリックします。
- 「Add another route」をクリックします。
- 宛先 (Destination) に対象 VPC の CIDR 範囲を入力します。
- ターゲット (Target) として「Peering Connection」と、そのピアリング接続の ID を選択します。

対象 VPC のルートテーブルに宛先を追加する
ピアリング先の AWS アカウントで、
- VPC ダッシュボードの「Route Tables」を選択します。
- 対象 VPC ID を検索します。
- 「Routes」タブの「Edit」ボタンをクリックします。
- 「Add another route」をクリックします。
- 宛先 (Destination) に ClickHouse VPC の CIDR 範囲を入力します。
- ターゲット (Target) として「Peering Connection」と、そのピアリング接続の ID を選択します。

セキュリティグループを編集してピアリング先 VPC アクセスを許可する
ClickHouse BYOC アカウントで、ピアリング先 VPC からのトラフィックを許可するように Security Group 設定を更新する必要があります。ピアリング先 VPC の CIDR 範囲を含むインバウンドルールの追加を依頼するため、ClickHouse サポートに連絡してください。
これで、ピアリングされた VPC から ClickHouse サービスへアクセスできるようになります。
ClickHouse へプライベートにアクセスするために、ユーザーのピアリング先 VPC から安全に接続するためのプライベートロードバランサーおよびエンドポイントがプロビジョニングされます。プライベートエンドポイントは、パブリックエンドポイントの形式に -private サフィックスを付けたものになります。例:
- Public endpoint:
h5ju65kv87.mhp0y4dmph.us-west-2.aws.byoc.clickhouse.cloud - Private endpoint:
h5ju65kv87-private.mhp0y4dmph.us-west-2.aws.byoc.clickhouse.cloud
任意ですが、ピアリングが正常に動作していることを確認した後、ClickHouse BYOC 用のパブリックロードバランサーの削除を依頼することもできます。
PrivateLink のセットアップ (AWS)
AWS PrivateLink は、VPC ピアリングやインターネットゲートウェイを必要とせずに、ClickHouse BYOC サービスへの安全でプライベートな接続を提供します。トラフィックは完全に AWS ネットワーク内で流れ、パブリックインターネットを経由しません。
PrivateLink セットアップの申請
ClickHouse Support に連絡して、BYOC デプロイメント向けの PrivateLink セットアップを申請してください。この段階で特別な情報は不要で、PrivateLink 接続を設定したい旨を伝えるだけで構いません。
ClickHouse Support は、プライベートロードバランサー や PrivateLink サービスエンドポイント を含む必要なインフラストラクチャコンポーネントを有効にします。
お使いの VPC にエンドポイントを作成する
ClickHouse Support 側で PrivateLink が有効化されたら、クライアントアプリケーションの VPC 内に、ClickHouse PrivateLink サービスへ接続するための VPC エンドポイントを作成する必要があります。
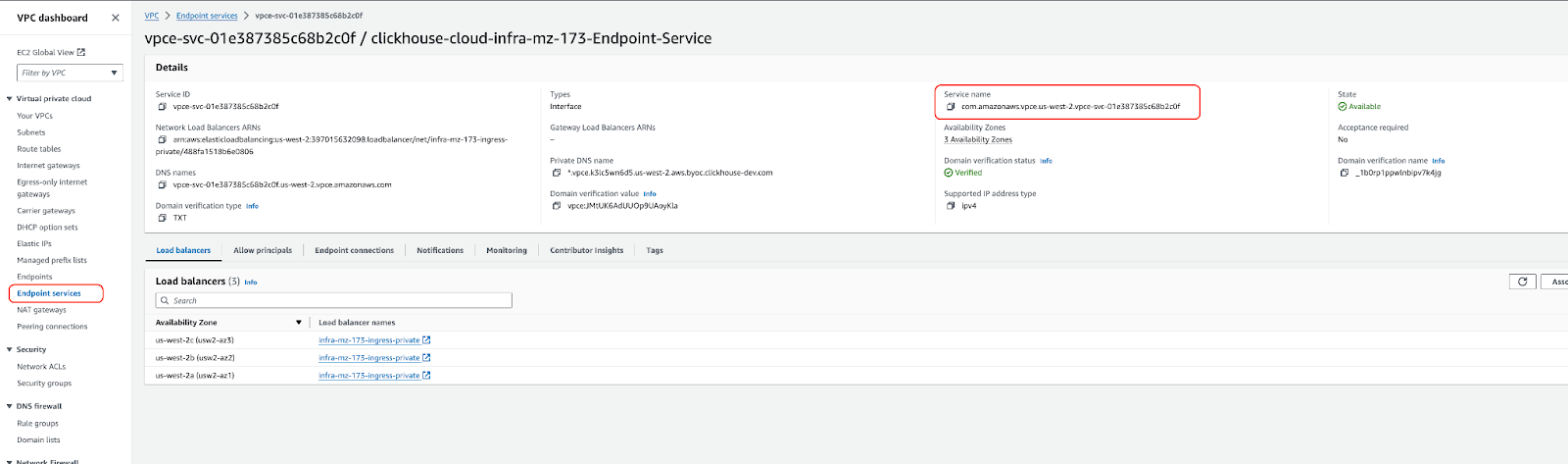
- エンドポイントサービス名を取得する:
- ClickHouse Support からエンドポイントサービス名が提供されます
- また、AWS VPC コンソールの「Endpoint Services」で確認することもできます(サービス名でフィルタするか、ClickHouse のサービスを探してください)
- VPC エンドポイントを作成する:
- AWS VPC コンソール → Endpoints → Create Endpoint に移動します
- 「Find service by name」を選択し、ClickHouse Support から提供されたエンドポイントサービス名を入力します
- VPC を選択し、サブネットを選択します(アベイラビリティゾーンごとに 1 つを推奨)
- 重要: エンドポイントで「Private DNS names」を有効化します — DNS 解決が正しく機能するために必須です
- エンドポイント用のセキュリティグループを選択または作成します
- 「Create Endpoint」をクリックします
DNS 要件:
- VPC エンドポイント作成時に「Private DNS names」を有効化してください
- VPC で「DNS Hostnames」が有効になっていることを確認してください(VPC Settings → DNS resolution および DNS hostnames)
これらの設定は、PrivateLink 用の DNS が正しく動作するために必要です。
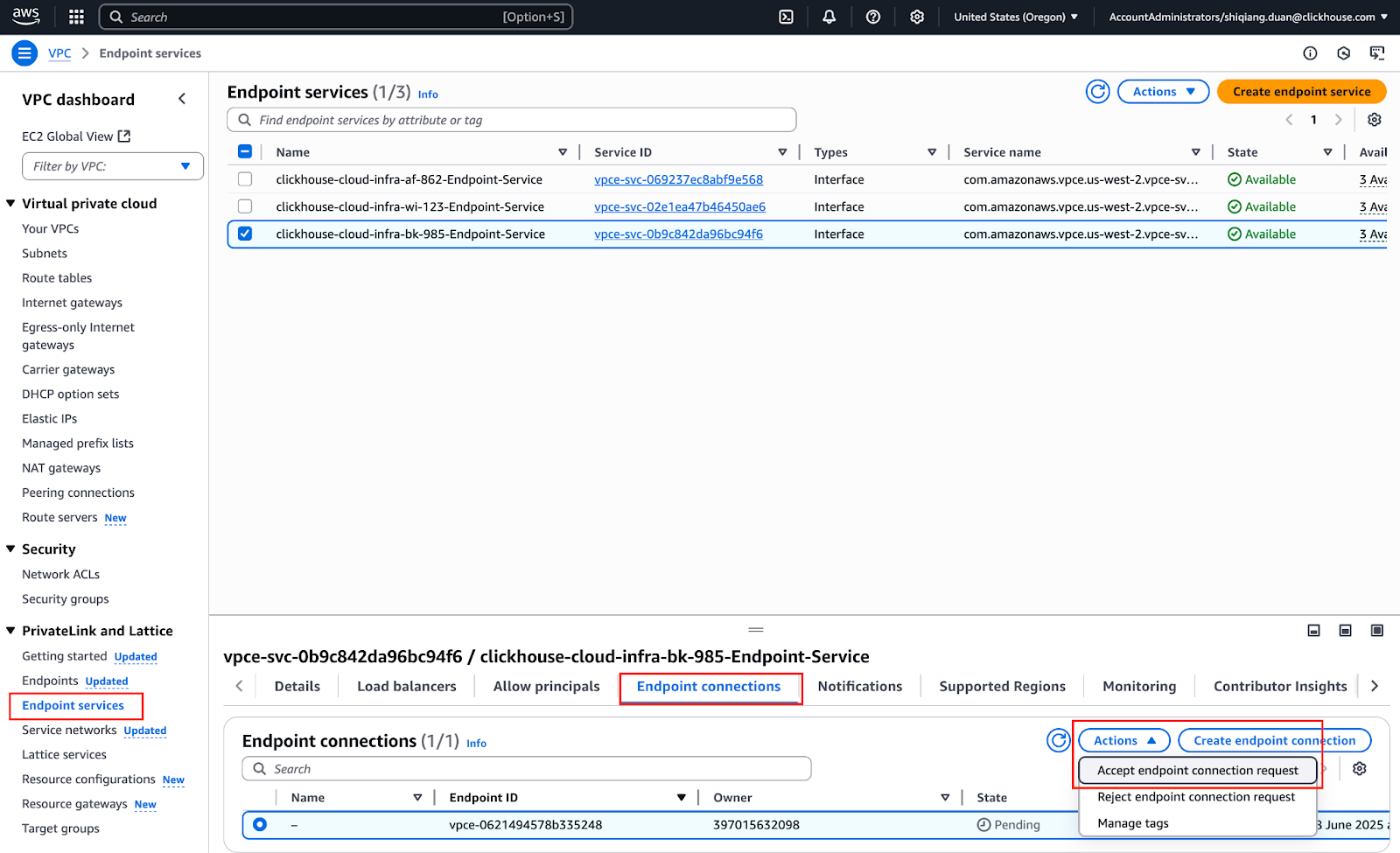
- エンドポイント接続を承認する:
- エンドポイント作成後、接続リクエストを承認する必要があります
- VPC コンソールで「Endpoint Connections」に移動します
- ClickHouse からの接続リクエストを見つけ、「Accept」をクリックして承認します
サービスの許可リストに Endpoint ID を追加する
VPC エンドポイントが作成され、接続が承認されたら、PrivateLink 経由でアクセスしたい各 ClickHouse サービスの許可リストに Endpoint ID を追加する必要があります。
-
Endpoint ID を取得する:
- AWS VPC コンソールで Endpoints に移動します
- 新しく作成したエンドポイントを選択します
- Endpoint ID をコピーします(
vpce-xxxxxxxxxxxxxxxxxのような形式です)
-
ClickHouse Support に連絡する:
- Endpoint ID(複数ある場合はすべて)を ClickHouse Support に提供します
- このエンドポイントからのアクセスを許可すべき ClickHouse サービスを指定します
- ClickHouse Support がサービスの許可リストに Endpoint ID を追加します
PrivateLink 経由で ClickHouse に接続する
Endpoint ID が許可リストに追加されたら、PrivateLink エンドポイントを使用して ClickHouse サービスに接続できます。
PrivateLink エンドポイントの形式はパブリックエンドポイントに似ていますが、vpce サブドメインが含まれます。例えば:
- パブリックエンドポイント:
h5ju65kv87.mhp0y4dmph.us-west-2.aws.clickhouse-byoc.com - PrivateLink エンドポイント:
h5ju65kv87.vpce.mhp0y4dmph.us-west-2.aws.clickhouse-byoc.com
VPC 内の DNS 解決により、vpce サブドメイン形式を使用した場合、自動的にトラフィックが PrivateLink エンドポイント経由にルーティングされます。
PrivateLink アクセス制御
PrivateLink 経由で ClickHouse サービスへアクセスする際の制御は、次の 2 つのレイヤーで行われます。
- Istio Authorization Policy: ClickHouse Cloud のサービスレベルの認可ポリシー
- VPC エンドポイントのセキュリティグループ: VPC エンドポイントに関連付けられたセキュリティグループで、VPC 内のどのリソースがそのエンドポイントを利用できるかを制御します
プライベートロードバランサーの「Enforce inbound rules on PrivateLink traffic」機能は無効化されているため、アクセスは Istio の認可ポリシーと VPC エンドポイントのセキュリティグループのみによって制御されます。
PrivateLink DNS
BYOC エンドポイントの PrivateLink DNS(*.vpce.{subdomain} 形式)では、AWS PrivateLink の組み込み機能である「Private DNS names」を利用します。Route 53 レコードは不要で、次の条件を満たすと DNS 解決は自動的に行われます:
- VPC エンドポイントで「Private DNS names」が有効になっていること
- VPC で「DNS Hostnames」が有効になっていること
これにより、vpce サブドメインを使用する接続は、追加の DNS 設定を行わなくても、自動的に PrivateLink エンドポイント経由でルーティングされます。
VPC Peering (GCP) および Private Service Connect (GCP)
GCP VPC Peering と Private Service Connect は、GCP ベースの BYOC デプロイメントに対して同様のプライベート接続を提供します。この機能は現在開発中です。GCP BYOC デプロイメントで VPC Peering または Private Service Connect が必要な場合は、提供状況およびセットアップ要件について ClickHouse Support にお問い合わせください。

